Defending Against onmicrosoft.com Spam
Over the past few months, I’ve experienced an increase in spam emails utilizing onmicrosoft.com as a means to bypass spam filters. These emails often include giveaway scams or more traditional tactics like the “full mailbox” or “full iCloud storage” scams.
After extensive manual remediation efforts, I’ve decided to take a comprehensive approach to mitigate this issue. As a result, I implemented a block on all emails originating from onmicrosoft.com domains.
You can use the following KQL query to check for similar emails in your environment. Be sure to replace mydomain.onmicrosoft.com with your onmicrosoft domain.
EmailEvents
| where SenderFromDomain has "onmicrosoft.com"
| where SenderFromDomain <> "mydomain.onmicrosoft.com"
| where SenderFromAddress !has "postmaster"
| where DeliveryLocation != "Blocked"
Assuming all of these are spam or phishing, you can implement the following transport rule in Exchange Online. Much like the KQL, be sure to replace mydomain.onmicrosoft.com with your onmicrosoft domain. In this rule we also allow senders with postmaster in the address to ensure bounceback emails from other Exchange Online mailboxes come through.
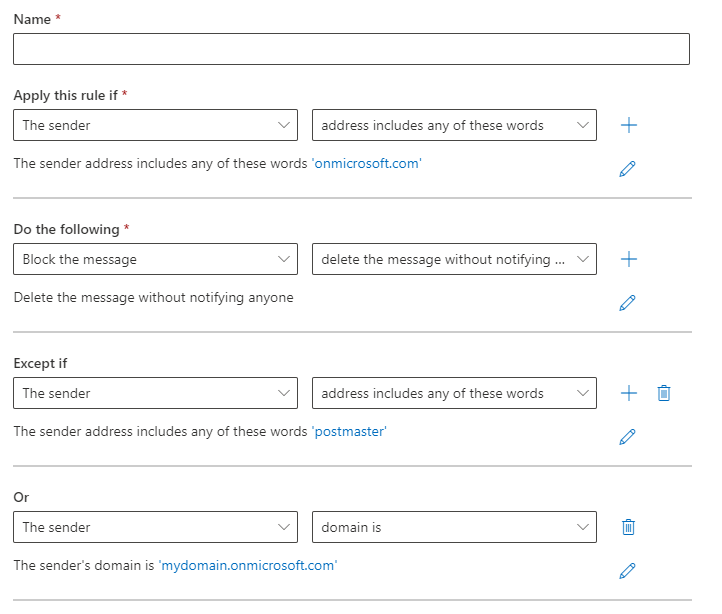
If you or your business are using an onmicrosoft.com domain, I strongly encourage you to follow the steps outlined in this article to set up a proper custom domain. Additionally, please ensure that you configure SPF, DKIM, and DMARC records to strengthen your email security.
Comments